Hack into a sci-fi near-future in an immersive, robust keyboard-only gameplay experience.
Type: Single-player
Genre: Strategy
Developer: LuGus Studios
Publisher: Iceberg Interactive
Release date: 13 October, 2021

Intro
Near-future science fiction is “set just far enough in the future to allow for certain technological or social changes without being so different that it is necessary to explain” (Encyclopedia of Science Fiction). Taking place about 40 years in our future, Midnight Protocol creates a remarkably robust and immersive gameplay experience using only keyboard commands – no mouse!
Game Universe
Taking place in Budapest in the year 2062, the player takes on the persona of Data, a hacker arrested one year prior after being doxxed who has recently been released due to insufficient evidence. Along with their allies Clover (a hacker trained by Data) and Snail (an information broker), Data sets out to learn how their identity was uncovered and why it was exposed.
The story unfolds slowly, which makes sense for a game where the action is occurring within a computer universe. Much of the terminology will feel familiar to players knowledgeable about computers, such as command, program, SysOp, boot, and more. The subtle use of leetspeak and textspeak builds a realistic world without seeming overdone. For example, Clover’s nom de guerre is written as C10v3r for her username. There are also some interesting terminology choices, such as the word ‘deck’ for the programs selected to be taken on a particular mission.
Gameplay and Mechanics
The Steam store describes Midnight Protocol as “a tactical narrative-driven RPG”. The flavor of a particular playthrough is influenced by the player’s choices. Reputation can be gained in three areas that influence what missions and programs become available. Grey hat reputation will be required no matter what as it relates to Data’s accomplishments and skill as a hacker. White hat reputation relates to making choices favoring ideals, while black hat reputation relates to criminal or selfish actions. While I agree the game is narrative-driven, I feel the gameplay and mechanics have more in common with turn-based strategy games. There are broadly two areas of play: the home console and networks.
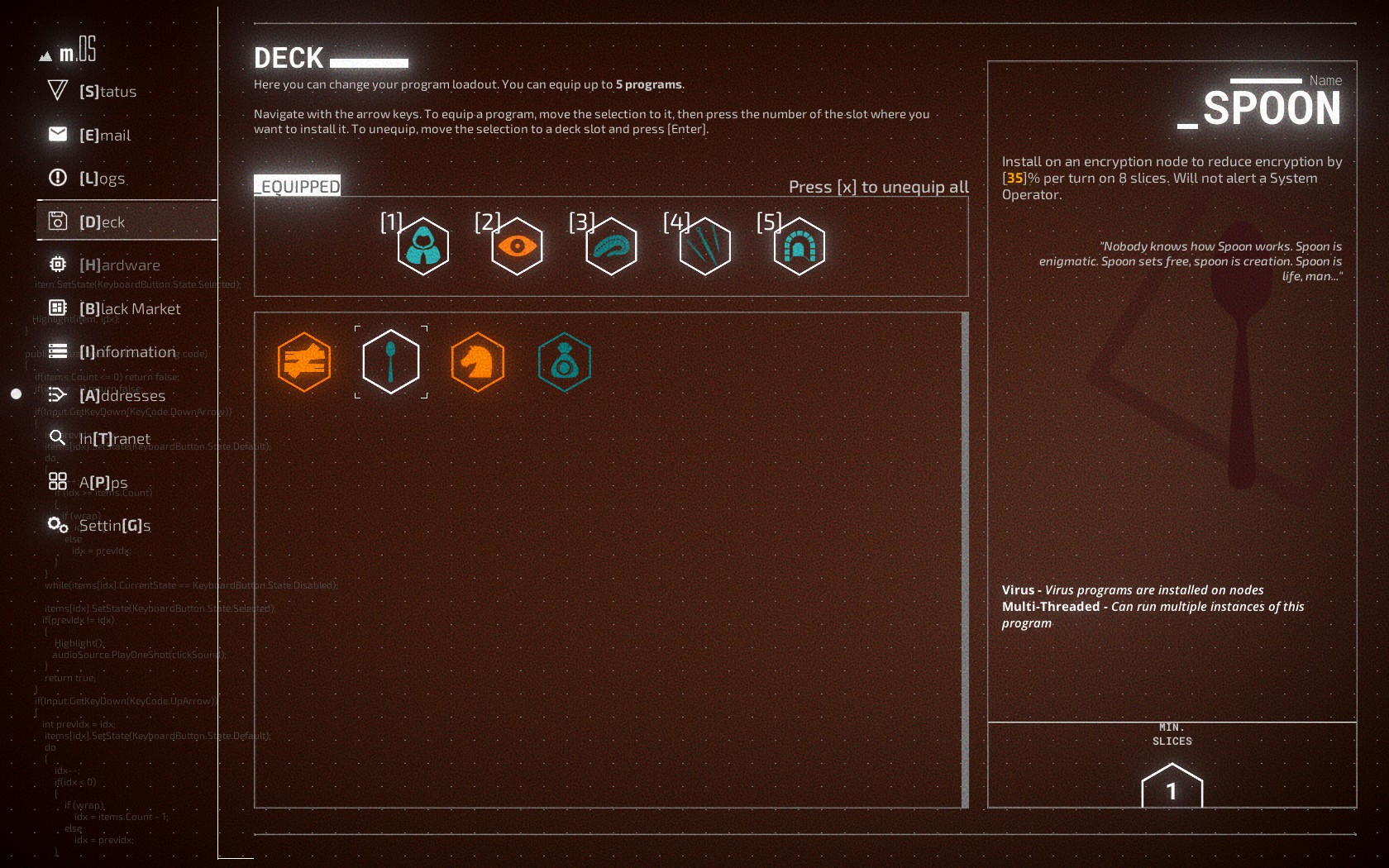
The home console is where much of the story progression takes place, through email conversations and performing research on the intranet, as well as preparing for missions. The Port Scanner under Addresses can provide useful information about a network, such as what types of nodes will be present or the length of the trace bar. The player can only take a limited number of programs, called a deck, with them on each mission, so part of the strategy is deciding which programs to choose. For example, the player may want to take the leech program to help siphon funds from finance nodes or the spoon program to help decrypt encryption nodes. It reminds me of deck-building games, which is perhaps why the developers chose the term. As the game progresses, the player can choose to buy new programs or hardware from the Black Market, as long as they have sufficient credits, so it’s important to be choosy about which programs to buy in what order.
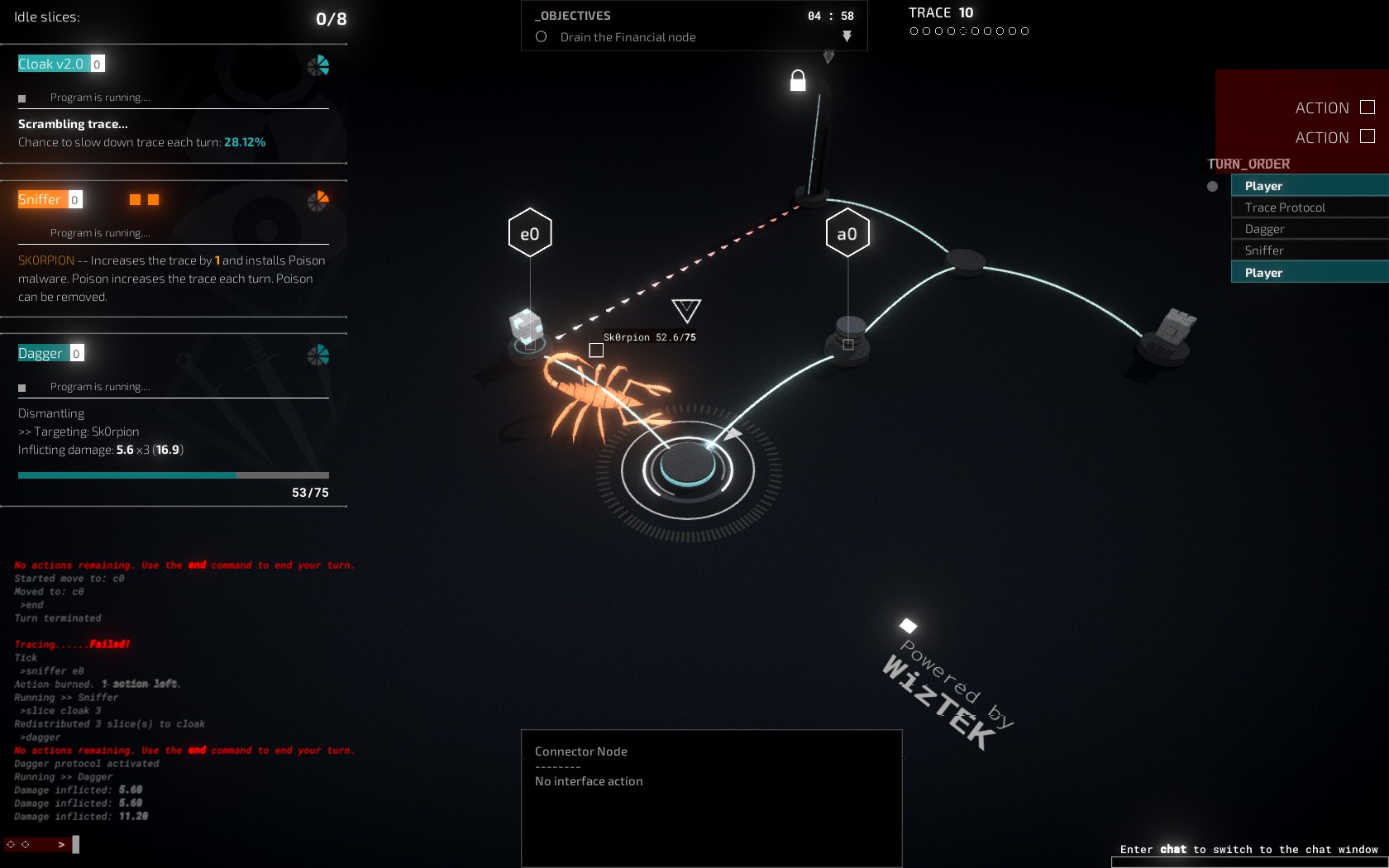
Networks are where the turn-based aspect of the game comes into play. The player has 2 actions per turn, which include commands like moving to an adjacent node, running one of the programs from their deck, or interfacing with a node. There are different types of nodes (e.g., finance, encryption, bridge, data), and the interface command will be different at each type. For example, at an access node the interface command can be used to remove three traces from the Trace Bar once per mission. Most networks have some level of static protection in the form of Intrusion Countermeasure Electronics (ICE). Triggering an ICE will cause nasty effects for the player and increase the trace. The player passes the turn to the AI by using the end command. The network tries to trace the player on its turn, and if it succeeds enough times to max the Trace Bar it causes problems, such as loss of credits or deleted programs. Some networks will also have a Systems Operator (SysOp) that patrols the connections and adds an additional layer of strategy and challenge. Being cautious and checking a connection for ICE before moving takes time, but moving without checking runs the risk of triggering an ICE, so the player must balance speed and risk. Managing the distribution of processing slices per program is an essential part of gameplay strategy. Some programs require a set amount of slices and run a set number of turns, while some programs’ effectiveness depends on how many slices have been assigned to that program. Leaving slices idle at the end of a turn generally leads to less desirable outcomes. Once the objectives have been met, the player can use the exit command to leave the network. Unless otherwise stated, a mission cannot be replayed once it has been completed, so it is important to confirm that the desired outcome has been achieved before leaving the network.
Art Style and Graphics
The art style of Midnight Protocol is minimalist, mainly using a monochromatic color scheme with purposeful noise reminiscent of analog television or VHS tapes. The home console user interface design is largely intuitive, and the player can choose from several themes to customize its appearance. All of the themes available at the start of the game are essentially monochromatic color schemes with varying levels of noise. There are additional themes that can be unlocked while playing, but I haven’t successfully done that yet in my playthroughs.
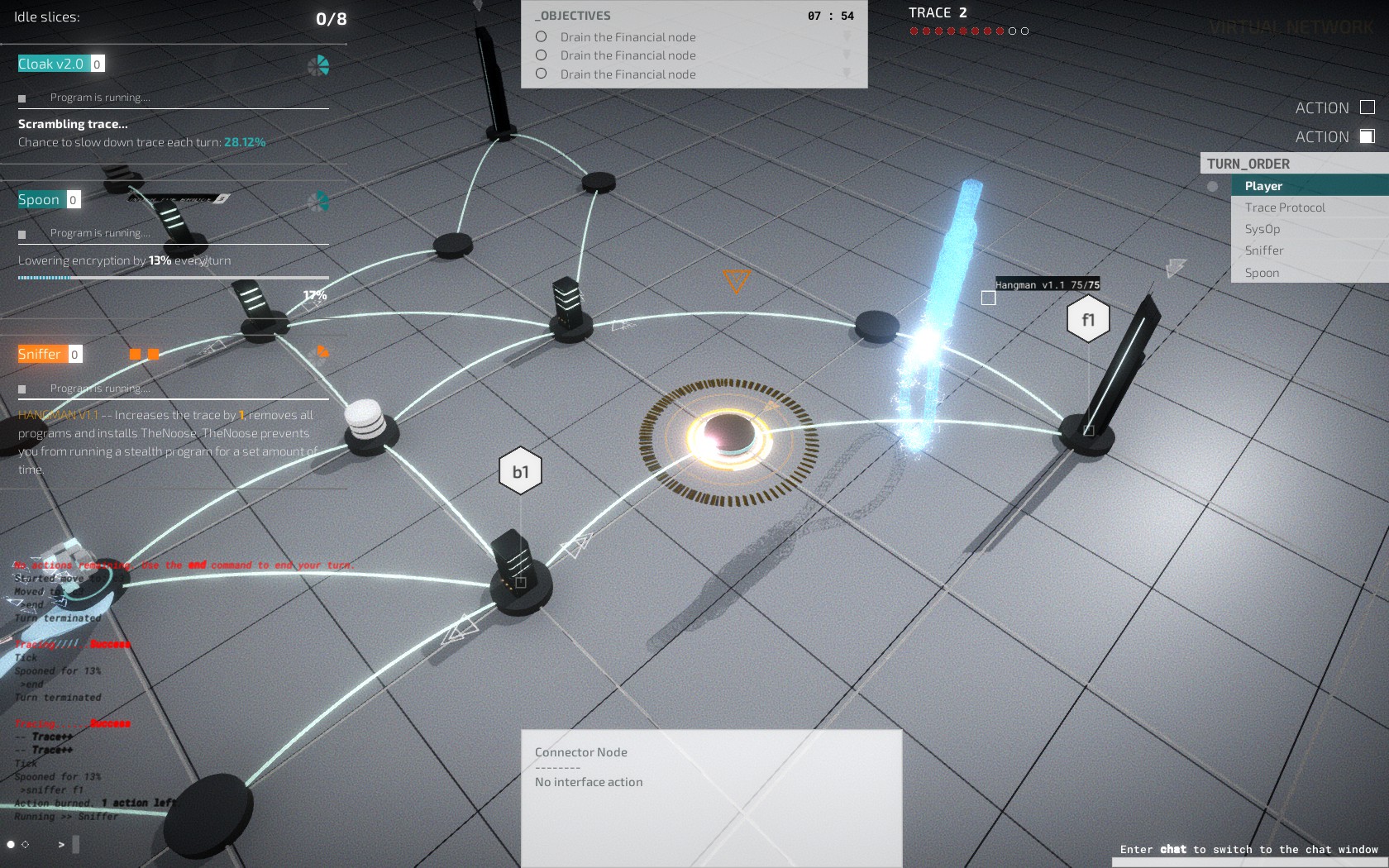
The visual representation of networks is where the game really shines. Different networks are visually distinct with consistent shapes for the node types. I found the default screen layout intuitive, but it is fully customizable if a player would prefer to change the location of components such as the Trace Bar or Objective List.
Sound and Music
The sound effects enhance the worldbuilding with typing as well as pinging, beeping, and other electronic elements on-brand for a hacker game, and the electronic aspects carry over into the music as well. The music of Midnight Protocol is emotive yet subtle, “letting your keystrokes become part of the soundtrack” as the Steam store description says. As of the time of review, I haven’t encountered any voice acting in the game, but this makes sense considering the game’s immersive style. I’m interested to see if the music changes in the later game, particularly with regard to how the story evolves with white hat, grey hat, or black hat reputation.
Verdict
Midnight Protocol offers hours of content between the main plotline and optional side quests, as well as Steam trading cards and 18 possible achievements, making its $14.99 price tag (as of the time of review) more than fair. One flaw that merits a mention is the inability to save manually, which hampers full exploration of the different avenues without significant repetition. Since the game’s release the developers have been responsive to making improvements to the gameplay experience, so my fingers are crossed that manual saving becomes an option sometime in the future. I haven’t finished my initial playthrough yet, but I’m enjoying my time in the Midnight Protocol universe. I would recommend Midnight Protocol to fans of hacking games and culture, the near-future science fiction subgenre, or keyboard-only typing games.










